Security Assessment Suite
Find Vulnerabilities Before the Breach
An organization’s security posture is defined by its most vulnerable point.Our Security Assessment Suite identifies and mitigates vulnerabilities within your infrastructure to ensure data protection and business continuity. With optional, flat-rate services, you can tailor the assessment to your specific needs.
These services are designed to help organizations:
Ready to talk about our assessment options?
Call a Connection cybersecurity expert today:
Our Approach to Security Risk Assessment and Remediation
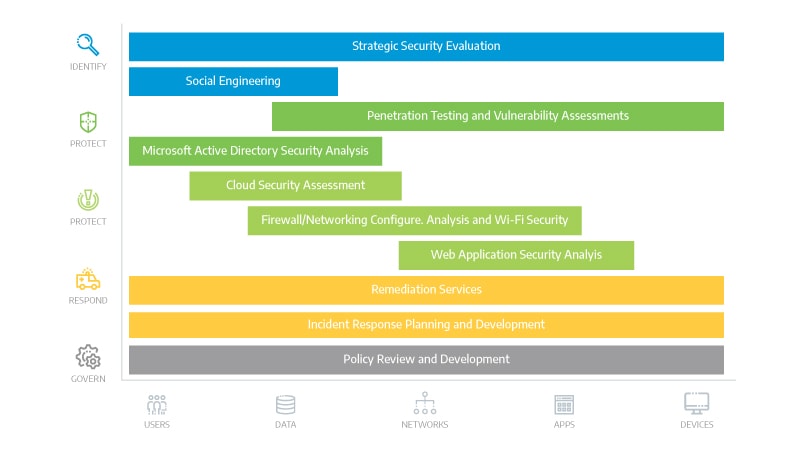
Connection customizes this service to identify vulnerabilities in your organization’s tools, systems, and policies. Our approach uses a series of optional, individual components to create a comprehensive security perspective, assessing the entire infrastructure instead of just individual components.- Internal and External Vulnerability Assessments
- Internal and External Penetration Testing
- Cybersecurity Network Assessments:
- Firewall, Switch, and Router Configuration
- Wireless Security Testing
- Cloud Cybersecurity Analysis
- Microsoft Active Directory Cybersecurity Analysis
- Web Application Cybersecurity Analysis
- Social Engineering and Security Awareness
- Security and IT Policy Review and Development
Why Our Security Assessment Suite?
A comprehensive cybersecurity assessment of your entire infrastructure is not just a precaution—it’s a critical necessity. Here’s why:- Interconnected System Protection: Mitigates risks across deeply interconnected IT environments
- Policy and Practice Alignment: Ensures security policies reflect and protect your current infrastructure
- Customized Risk Profile: Provides insights tailored to your organization’s specific tools, systems, and policies
- Proactive Threat Mitigation: Identifies vulnerabilities before they’re exploited, reducing risks of breaches and operational disruptions

Evolving Trends in Malware Analysis
The landscape of malware analysis has significantly evolved, driven by the increasing sophistication of cyber threats and the advanced techniques being developed to combat them. Explore the key trends shaping the field of malware analysis.Cybersecurity Specialists with Decades of Field Experience
Connection’s cybersecurity specialists have spent years protecting organizations’ data availability and privacy across a range of industries. Each specialist is equipped with the skills and certifications to make each project a success. Connection’s cybersecurity specialists work as trusted advisors with our clients, creating custom solutions to meet your organization’s specific needs.
Cybersecurity Assessment Flyers
Ready to talk about Cybersecurity Assessment and Testing?
Call a Connection expert today.
Let’s Connect!
Share your email and a Connection Cybersecurity Expert will reach out to you during our business hours.Connection Community
TechSperience Episode 140: Signals of...
In this episode, the Connection Security Center of Excellence Team takes us on a journey—both literal and technical—sharing insights gained... Read More
Data Security and Compliance: Strengthening...
Data security is a critical priority for everyone, especially those who manage sensitive information across a variety of workstreams within... Read More
Future Proof Your Business with Microsoft Azure
Keeping up with ever-evolving cloud technology is imperative for businesses to thrive. That’s why we’re excited to introduce our four-part... Read More
Reimagining Manufacturing IT: Building a...
Manufacturing is at a pivotal moment. Industry 4.0 has evolved from buzzword to baseline, and leaders are now tasked with... Read More
TechSperience Episode 137: Quantum Computing...
Quantum computing represents a significant shift in computational power, offering both opportunities and challenges for securing sensitive data. Join the... Read More






