This website stores cookies on your computer.
These cookies are used to collect information about how you interact with our website and allow us to remember you. We use this information in order to improve and customize your browsing experience and for analytics and metrics about our visitors both on this website and other media. To find out more about the cookies we use, see our Privacy Policy.
Fortinet Product Showcase
The Fortinet Security Fabric: Cybersecurity, Everywhere You Need It.

One Platform to Converge, Consolidate, and Consume AI-driven Cybersecurity
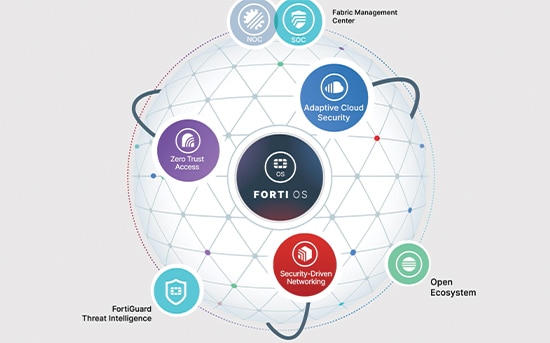
Within the Fortinet unified platform, three solutions redefine cybersecurity, helping you to respond to an ever-evolving cybersecurity landscape to meet constantly accelerating business needs. The solution to simplifying complex networks, distributed users, and hybrid applications is the convergence and consolidation of Secure Networking, Security Operations, and Unified SASE.
Secure Networking
Digital acceleration has led to a rapid expansion of attack surfaces and creation of new network edges, including LAN, WAN, 5G, remote workers, and clouds. Fortinet’s Secure Networking approach is the industry’s only converged networking and security platform. This convergence enables AI-powered defense of today’s highly dynamic environments while enabling better productivity and user experience.Security Operations
The Fortinet Security Operations (SecOps) platform seamlessly integrates behavior-based sensors to detect and disrupt threat actors across the attack surface and along the cyber kill chain. Centralized investigation and remediation can be orchestrated, automated, and/or augmented to reduce cyber risk, cost, and operational effort.
Unified SASE
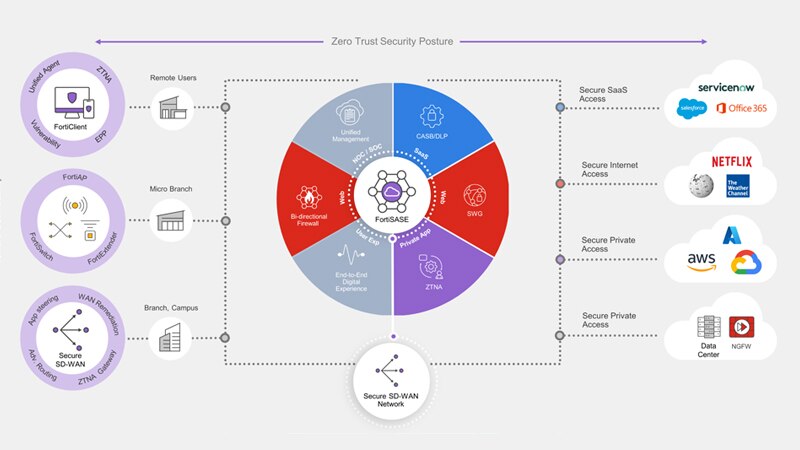
Fortinet Unified SASE is a cutting-edge cloud-centric networking and security solution specifically designed for the hybrid workforce, powered by a single OS, and unified management. It includes a high-performance and scalable cloud network, and best-in-class AI-powered security such as universal ZTNA, a unified agent, secure SD-WAN, and digital experience monitoring. Unified SASE solution ensures the utmost security for all edges, devices, and users, whether they are accessing the Web, corporate applications, or SaaS applications.Securing OT with the OT Security Platform
As industrial environments increase connectivity with external and internal applications and corporate IT networks, critical OT assets are exposed. IT and OT silos hinder the deployment of a cybersecurity strategy capable of mitigating threats in real time. The results can be devastating with the potential to disrupt critical infrastructure, resources, and services serving communities.Fortinet Enterprise-grade SMB Security
With Fortinet, lean IT teams can quickly deploy however it suits them, on-premises or in the cloud. Consistent security is maintained regardless of where data resides, how users connect, or how the business shifts across network, endpoint, and cloud security.- Unified networking and security to simply deployment and support
- Integrated endpoint security to support hybrid workforces
- Centralized management and broad reporting and analytics
FREE Assessment
A Fortinet Cyber Threat Assessment can help you better understand:Security Risk: What application vulnerabilities are being used to attack your network, which malware/botnets were detected, what phishing attacks are making it through your defenses, and which devices are a security breach probability.
Productivity: Which peer-to-peer, social media, instant messaging, and other apps are running. For application visibility/control, what spam, newsletters, or adult content are affecting your email.
Utilization and Performance: What are your throughput, session, and bandwidth usage requirements during peak hours for the network, email system, and critical applications.
Fill out the form below, and we’ll get you started with your FREE threat assessment.
Read Transcript
Batch Add Products by Item #
13